Why is it that I stumble upon a smartphone artifact that drives me bonkers around holidays??? I am in the midst of the FOR585 course updates and I go through everything in great detail during this time. I expect to see major changes in a full version update (aka iOS 10 to iOS 11 or Android 7 to Android 8) but seeing artifacts hop around (bunny reference there just in case you missed it) in the minor steps of updates (iOS 11.2.5 to iOS 11.2.6) is not something I like. I don’t like it because it makes even more work for me and for you!
As I am writing this, I am updating to iOS 11.3. I hope to have that added into this blog by the end. For now, my research is based on what I noticed when examining 11.2.5 and 11.2.6 in great detail. The Apple Maps is different, inconsistent and just doesn’t make sense. All of the Apple Maps uncertainty started in the minor updates of iOS 10. I wrote a blog about it titled “How the Grinch Stole Apple Maps.” Read it for all of the details. I am going to summarize what the “Grinch” did.
To do my Grinch blog, I tested the following devices. (Again, a special thanks to my trusting friends and family for granting me access to their devices.)
- iPhone 6s with a fresh install of 10.0.2
- iPhone 7 updated from previous iOS versions running 10.0.2
- iPhone 6s updated from previous iOS versions running 10.0.2
- iPhone 7 updated from previous iOS versions running 10.2
- iPhone 6s with a fresh install of 9.3 – jailbroken
- iPhone 6s+ with a fresh install of 10.1.1
- iPhone 6 updated from previous iOS versions running 10.1.1
- iPhone 6s+ updated from previous iOS versions running 10.2
- iPhone 7 updated from previous iOS versions running 10.1.1
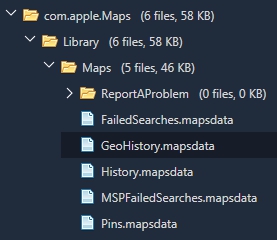
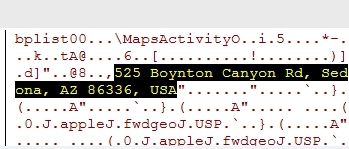
I was attempting to find where Apple Maps was storing my search requests and directions since I couldn’t find them in GeoHistory.mapsdata or the older history.mapsdata.
For each of these devices, I opened Apple Maps and searched for items I could easily identify:
- Radio City Music Hall, NYC
- Malvern Buttery
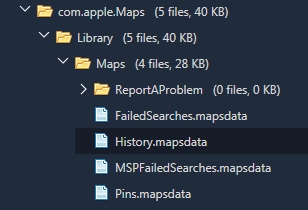
So, when I was just updating my slides, I decided to take a look at my iPhone again (running 11.2.6) and verify the file paths. I was SHOCKED to see that the GeoHistory.mapsdata was gone. Literally, not even there. Did the Easter Bunny hide it or did the Grinch steal it completely?

Before, he appeared to be snatching the new data and being evil and allowing you to see the old stuff. But where the heck are my searches and where did my file go? I honestly even considered that Apple reverted back the history.mapsdata because that file is still present, but that isn’t the case.
What’s a girl to do next? PANIC and then I phoned a few friends and asked them to try to find GeoHistory.mapsdata on their devices (thank you Lee and Mattia for testing with me) and ultimately went back to my first blog post on it and read it again. Sometimes revisiting your old work can spark something in your mind. One major thing that I took away from reading that blog post again is this:
“*Note: Some of the devices below are syncing with iCloud and some are not. I wanted to be thorough and make sure that the Grinch didn’t take the file to the cloud…”
Could it be that the Easter Bunny did what the Grinch had envisioned and hid the GeoHistory.mapsdata in iCloud? We know the bunny is tricky and this year Easter falls on April fools, so we should expect anything. Here is what I tested and found (so far) during my hunt for this file.
The following test devices were used:
- iPhone 6s with a fresh install of 11.2.5
- iPhone 7 updated from previous iOS versions and currently running iOS 11.2.6
- iPhone X updated from previous iOS versions and currently running 11.2.6 (being updated to 11.3 as I type)
- iPhone 7 with a fresh install of 11.2.5
- Many backups from all of my test devices
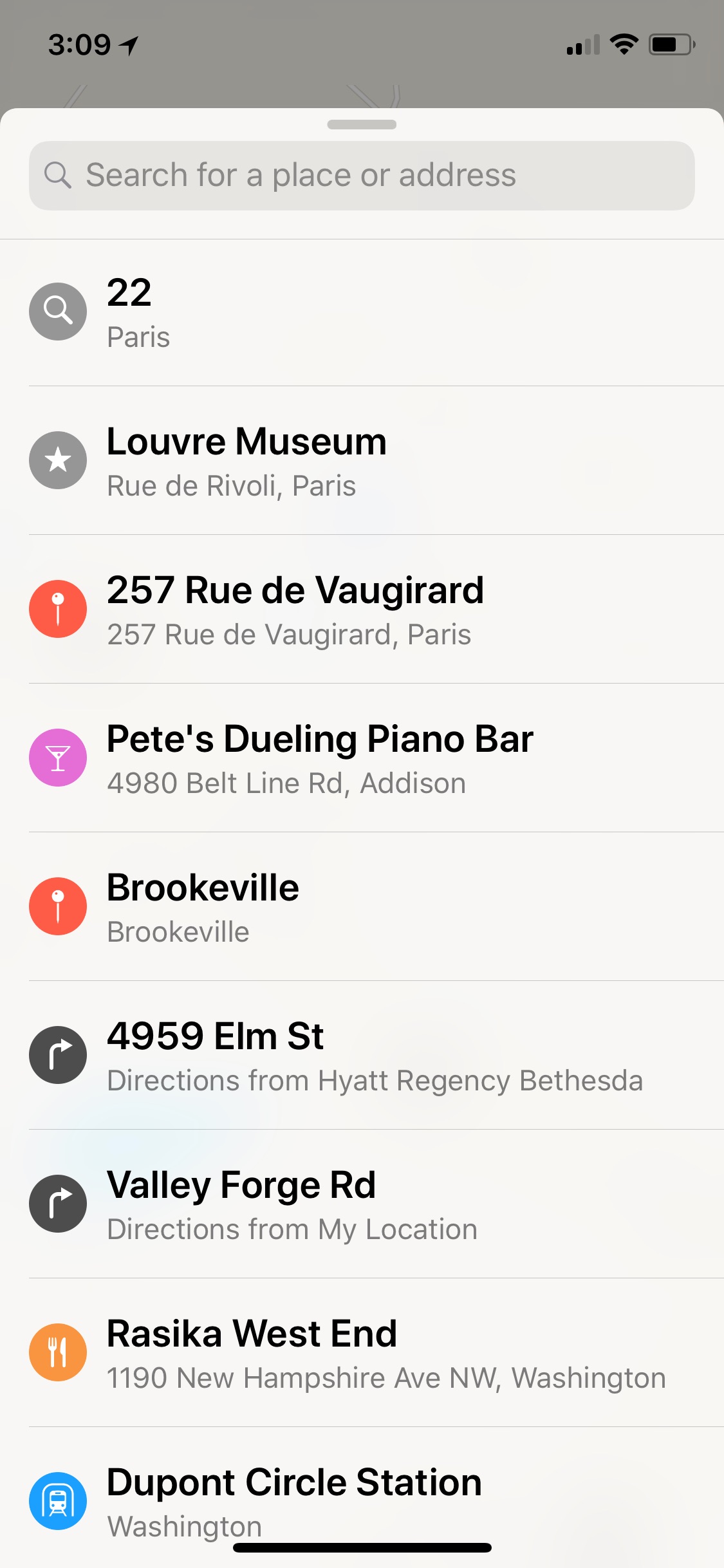
My iPhone is the iPhone X (listed above and I know I searched for locations in Dallas, Panama and in Paris on recent trips. I rarely use Apple Maps (probably because the Grinch killed it for me) so I rely on it only when Google Maps and Waze let me down. The iPhone 6s is a test device that I have searched for directions many times in Apple Maps. It makes testing so much easier when you know what data you expect to find. Here is what Apple Maps looks like on my iPhone X.
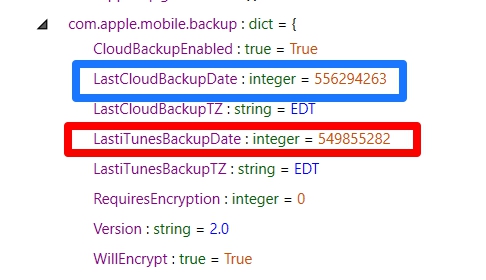
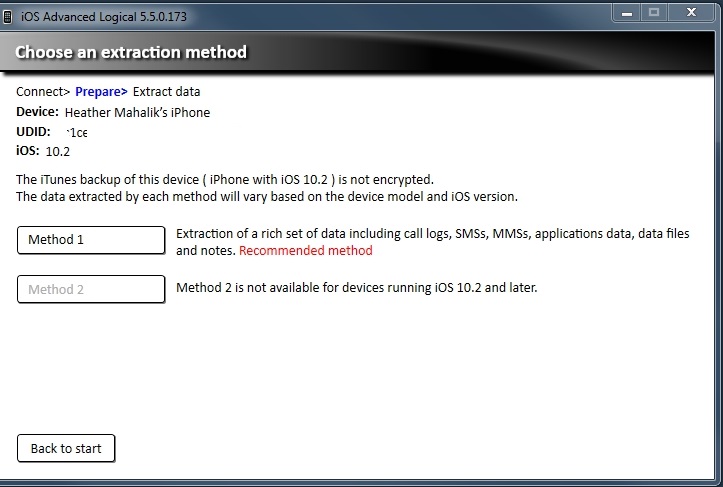
Once all data was populated, I conducted both iTunes/iCloud backups and Cellebrite Physical Analyzer File System dumps (Methods 1 and 2) to quickly acquire the data. I even tried looking at my attached device live in BlackLight and iBackupBot. I tried parsing the data dumps in BlackLight, Oxygen Detective, Magnet AXIOM, Cellebrite Physical Analyzer and manual examination to ensure I wasn’t overlooking something. I pulled my own iCloud data with Elcomsoft and searched for the file in those backups and still didn’t find exactly what I was looking for – wait for it…
When I manually examined the file system of the backups and data dumps, I started to see major inconsistencies just like I did in iOS 10. The GeoHistory.mapsdata file was sometimes present and sometimes not. The history.mapsdata file was there no matter what. History.mapsdata, contains legacy searches in Apple Maps, it does not contain any data since iOS 8. If you don’t see this file, chances are the user didn’t have a device running iOS 7 that they updated from (aka, they either started fresh with iOS 8 or a newer iOS version).
Based upon my experience with iOS device forensics, it seems that when Apple no longer uses a file, the file persists and is no longer updated. When Apple wants to protect a file, they encrypt it and/or make it inaccessible without a full physical image, which is currently not possible on new devices without a jailbreak.
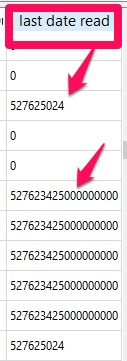
What I found is that some of the devices running versions ranging from iOS 10.0.2 – 11.2.5 had GeoHistory.mapsdata with older Apple Maps content. None of the devices running iOS 11.2.6 have GeoHistory.mapsdata. This is insanity. Again, I believe if Apple doesn’t want you to see something they encrypt, restrict or hide it.
I promised to keep hunting for you and what better time to hunt than Easter. So, where the heck is this darn file hidden? Well, the Easter Bunny got crafty and hid it in the cloud. Before doing what is listed below, you need to make sure you have legal authority or written consent from the user to access their cloud data. You also need their credentials.
I used Elcomsoft Phone Breaker to first pull iCloud, which I previously mentioned, and didn’t find anything further than what iTunes had presented. Then I pulled the “Synced data” from iCloud. (Thanks Mattia for providing me your results as well!)
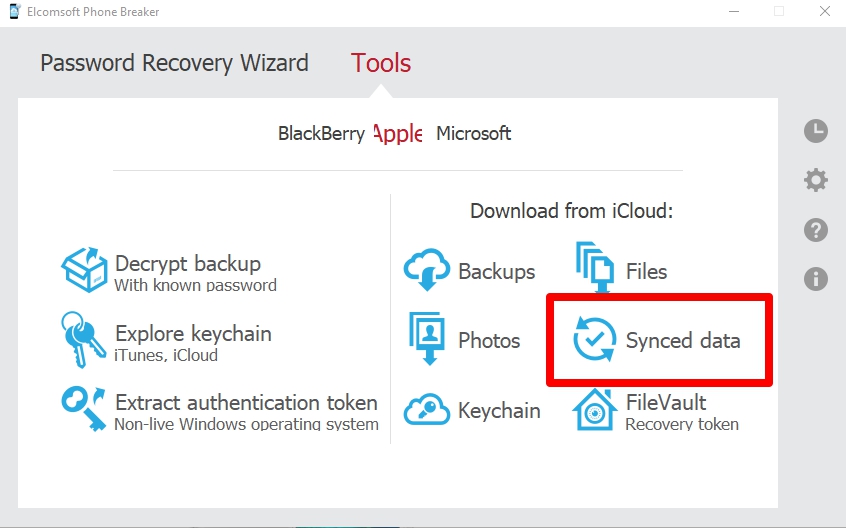
I then entered my iCloud credentials and my PIN for 2FA (yes, this is required the first time you use the tool and will alert the user – user caution here).
From here, I was presented with a list of options to pull from synced iCloud data. Since this is all about Apple Maps, that is all I selected. If you want to learn about the others, I suggest you sign up for FOR585 Advanced Smartphone Forensics (shameless plug- for585.com/course).
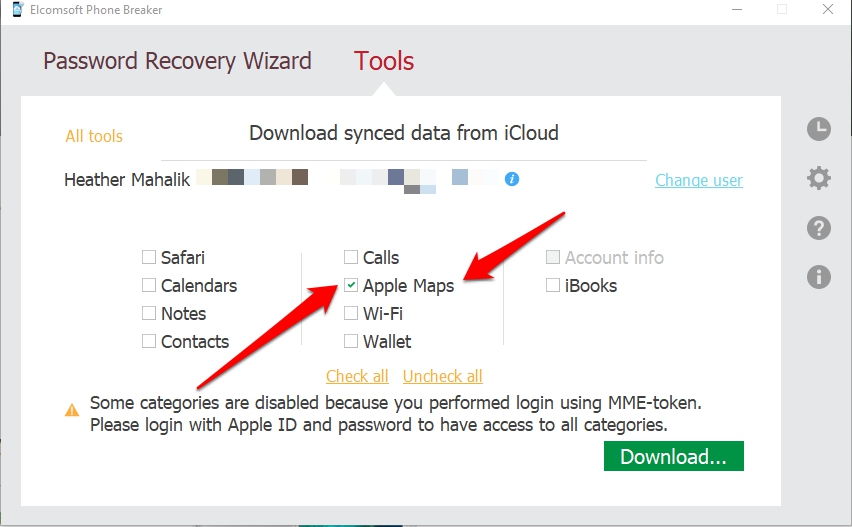
What I found when I opened this file blew my mind. I expected this of Apple, so I shouldn’t be shocked, but I couldn’t believe that the crazy Easter Bunny decided to hide my Apple Maps in iCloud. I am just thrilled that I can access some, if not all of the history. Side note: the user must sync to iCloud or you will not find it here. 🙁
To examine the results, Elcomsoft creates an AppleMaps.db file that I examined manually and a file that can be opened in Elcomsoft Phone Viewer. Let’s start with Phone Viewer, because let’s be honest, most people like for a tool to show them the results. (Click on the image to see the graphic in a zoomed in format.)
In Elcomsoft Phone Viewer, I started examining searches and saw everything from Paris and Panama that I searched for in addition to other historical searches. This is great news, but let’s keep going because these could just be generic searches where the user didn’t request directions.
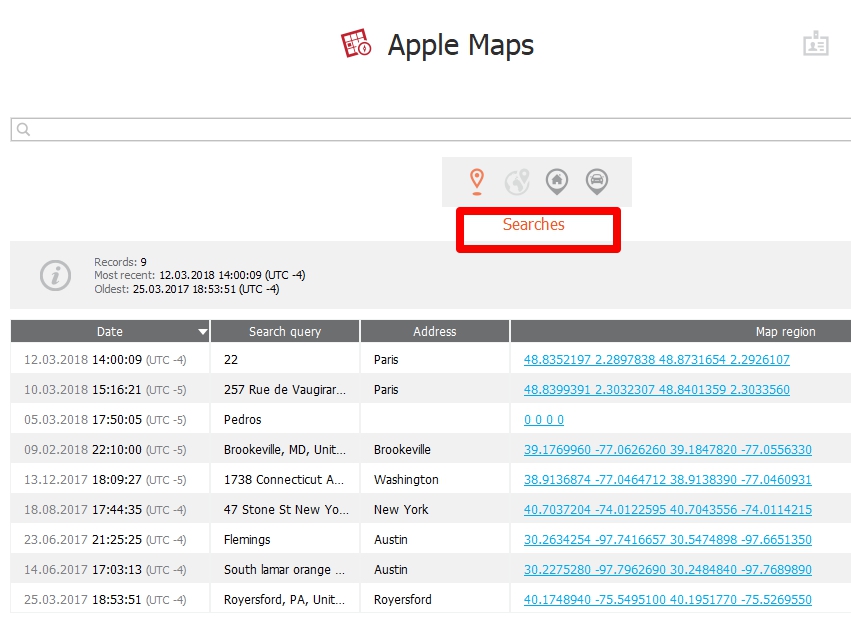
Next I looked at explored places and found other searches that I performed on my iOS device, but not necessarily in Apple Maps. However, when you search for something on an iOS device, the device assumes you may ask for directions and caches that info.
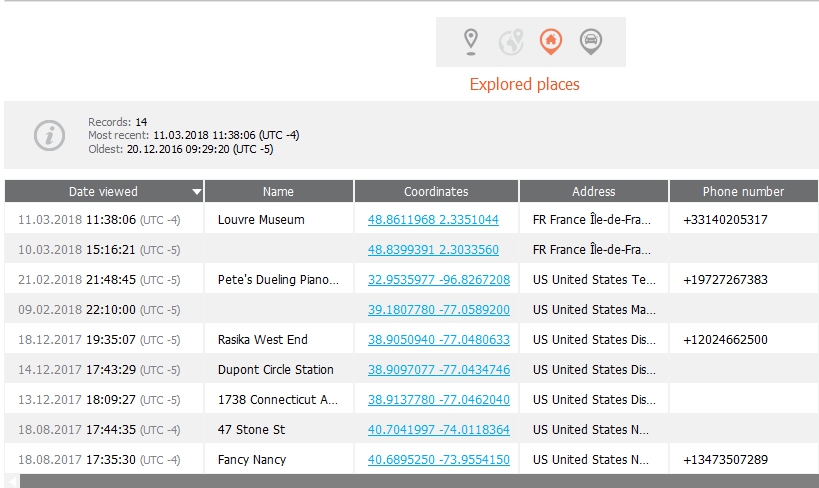
Finally, we find the directions the user searched for. Best part, we get to see how the requested the directions (walk, drive, transit, fly, etc.) Pretty cool stuff.
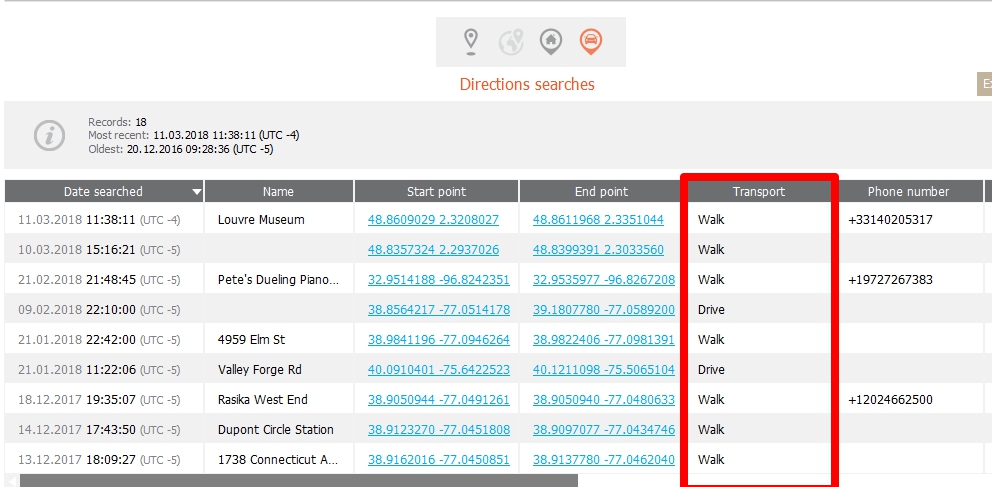
Thanks to Mattia, I can even show just how far back some of these artifacts span… Again, I am not a huge fan of Apple Maps, so seeing dates from 2015 in Mattia’s data is pretty sweet. Below we can see searches from 2015.
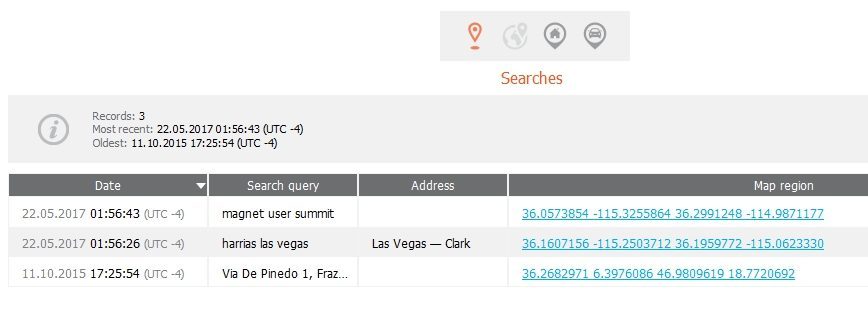
Mattia also had directions from 2015.
The databases can be used as well. This is really helpful if you like to write SQL queries to parse these artifacts. This database is created by Elcomsoft and isn’t something you are going to find on the device. It’s strictly iCloud based. The table provided is called AppleMaps.db. There are several tables provided. You need to determine what is relevant to your investigation, but I recommend during a cursory glance of all of them.
I wrote a simple query to parse the DirectionsSearch table. Please do not copy and paste from this blog. WordPress does some funky formatting the SQLite doesn’t like. Grab it here: AppleMapsQuery.txt
SELECT
datetime(timestamp,’UNIXEPOCH’,’localtime’) AS “Timestamp”,
name,
start_point_name,
start_point_latitude,
start_point_longitude,
end_point_latitude,
end_point_latitude,
telephone,
url,
transport_type AS “0-Drive, 1=transit, 2=walk”,
start_point_is_current_location AS “Start Point:1=Current Location”
from DirectionsSearches
order by timestamp desc
This query found all of the directions I searched for including the pesky Malvern Buttery and Radio City Music Hall, which I was searching for in my Grinch post.
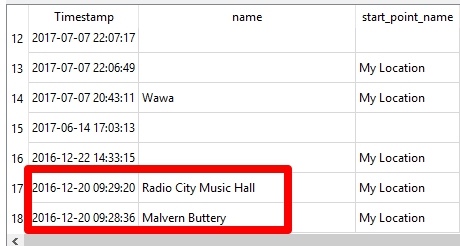
Now I am wondering if the Grinch is in cahoots with the Easter Bunny and it was hidden here all along. :/ This is why we keep testing and digging. This is why we need more than one tool. This is why we have to get out of our own way and start trying to new methods and tools. I also plan to keep testing the cloud capabilities of the other tools to include in my FOR585 update.
Just as I was done writing, my update to iOS 11.3 completed. I did a simple Apple Maps search for directions to Jim’s in Philadelphia. (Another thanks to Lee for introducing me to Jim’s in 2003! Here, you will get the world’s best cheesesteak.)

I forced my device to backup to iCloud and repeated all of the steps above. Everything appears to be the same and Elcomsoft was able to parse my search from the Synced data. And unfortunately, the GeoHistory.mapsdata is still missing from the file system image.
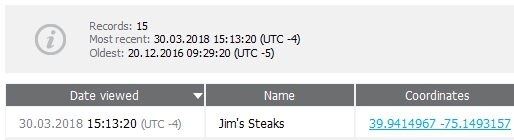
All of this was done with the demo version of Elcomsoft Phone Viewer. If you want to try a tool, ask the vendor. Most will give you at least a free demo. Not one tool can do it all, so get out there and help me hunt! Oh, and Happy Easter.
Other things you may want:
Files of interest on the device (if the plist appears to be Base64 encoded use Oxygen Detective’s Apple plist Viewer):
Note: For graphics on what these files look like and the paths for each data dump, refer to the Grinch blog.
/var/mobile/Applications/group.com.apple.Maps/Library/Preferences/group.com.apple.Maps.plist
/var/mobile/Applications/com.apple.Maps/Library/Preferences/com.apple.Maps.plist
/var/mobile/Applications/com.apple.Maps/Library/Maps/history.mapsdata
/var/mobile/Applications/com.apple.Maps/Library/Maps/GeoHistory.mapsdad