Monthly Archives: February 2016
Zdziarski Summary
Everyone is asking me to comment on the iPhone 5C. Here is my comment: “Well said, Jon.”
Please read his blog post.
Can’t Crack into that iOS device?
Good afternoon everyone! One of the most common questions I get is in regards to accessing locked iOS devices. My first response is always, “it depends.” Anyone who conducts smartphone forensics on a regular basis knows that nothing is consistent and that there always seems to be a way around a hurdle, but that is not always true when dealing with iOS.
For newer 64-bit iOS devices, if they are locked and you don’t have access to the passcode, the pairing/lockdown file and the device is not jailbroken, you are going to have a hard time successfully getting into the device. I recommend trying all tools available to you, just to make sure you have tried everything! Elcomsoft provides physical support for jailbroken 64-bit devices, and it may work for you, so try it if you have access to the tool. Or ask for a demo! You never know when it may be your lucky day.
Before researching your options, you have to know the version on the device, if you don’t know the version, you can obtain in on a Mac by using libimobiledevice from http://www.libimobiledevice.org/ and running ideviceinfo. This method will work on locked iOS devices, enabling the examiner to identify the iOS version they are facing on the device. Simply follow these steps:
- Launch Terminal
2. Type the command below to create the libimobiledevice-macosx directory on the user’s desktop and place the libimobiledevice command-line tools into it.
$ git clone https://github.com/benvium/
3. Navigate to the libimobiledevice-macosx directory, as follows:
$ cd ~/Desktop/libimobiledevice-
4. Create and edit the .bash_profile file using the nano command, as follows:
$ nano ~/.bash_profile
5. Add the following two lines to the .bash_profile file, as follows:
export DYLD_LIBRARY_PATH=~/Desktop/
macosx/:$DYLD_LIBRARY_PATH
PATH=${PATH}:~/Desktop/
6. Press Ctrl + X, y and hit Enter
7. Return to the terminal and run the following command:
$ source ~/.bash_profile
Your device information will be displayed. 🙂
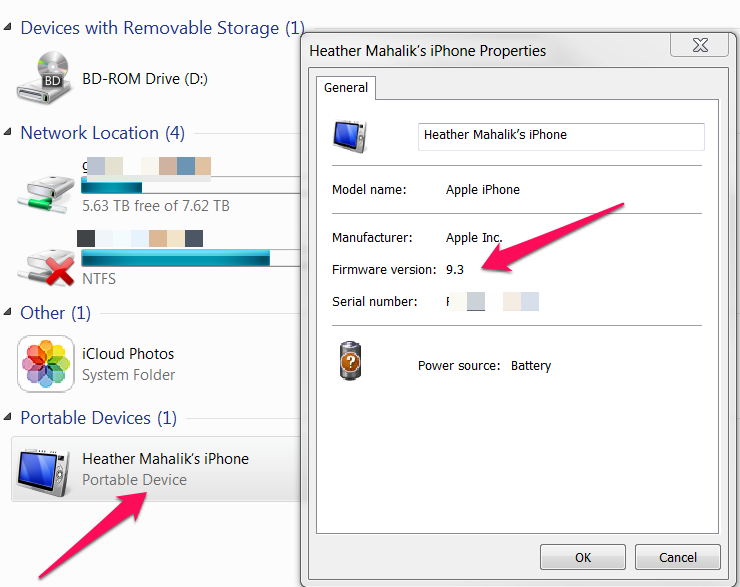
On a Windows platform (version 7 or later), simply plug the iOS device into a PC that does not have iTunes installed and follow these steps:
- Plug the iOS device into the PC
2. Go to My Computer
3. Right click on the iOS device
4. Select Properties
Today, Dylan Dorow, kindly shared some useful cheat-sheets on what’s currently possible for locked iOS devices. They are attached below and are available for download in my Reading Room. These are extremely useful when trying to decide what is possible for accessing a locked iOS device.
iDevice_Make_Model_and_iOS_version iOS_Device_Bypass_WorkFlow
Good luck cracking those devices! And make sure you stay current on what the tools are capable of supporting because it changes quickly!