I’ve realized just how important it is to blog vs just do a webcast when I was completing my course updates. I would stumble upon a webcast, but didn’t have time to watch it, so I looked in another direction. This made me realize that I should write down everything I put into a webcast. Will a webcast hold up in course? Do you have time to watch all of them? Seriously, I am curious about the impact so please let me know.
In 2019 – I am going to write down what I talk about in webcasts. If I have the time, I may try to blog about my speaking events as well (think Keynotes and SANS @Nights). Some blogs may be short and sweet, but this way when someone says, “how can I do X” I will point them to my blog. 🙂

To kick this one off, I am going to simply discuss a file that stores information on how an iOS device was setup. This is a file that I am asked about a few times a week. In many cases, it matters if the user synced from iCloud, started from scratch or restored from iTunes. So here goes!
First, you should be obtaining an encrypted backup at a minimum. If you have the ability to get a full file system dump, even better. Without encryption, I cannot guarantee that all of the files I plan to discuss in upcoming blogs will exist. Make sure your analytical tool of choice will decrypt the data. If you are trying to do this for free follow the steps below.
Creating and parsing an encrypted iOS backup for FREE:
- Launch iTunes on your forensic workstation. Update if necessary.
- Make sure you Trust the computer on the iPhone.
- Create an encrypted backup with a password you will remember (yep, people forget all of the time!)
- If you aren’t using a commercial tool or one that supports decrypting the backup, you may have to get crafty. I stumbled upon AnyTrans during my updates and it’s pretty sweet. To use this, you must know the password or crack it (refer to other blog posts in my archives.)
- Launch AnyTrans and it will show you if you have locked backups.
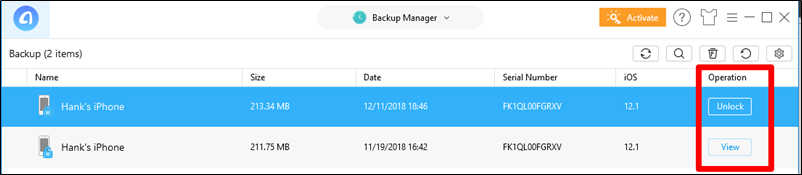
6. Select the locked backup (you know it’s locked because the option is to “unlock” it.
7. Enter the password and the backup will be unlocked! The top portion shown below is how the backup directory will look. The original backup remains and the unlocked version is called BackupUnlock. If you peek inside that directory, you will find the backup with the date it was unlocked.
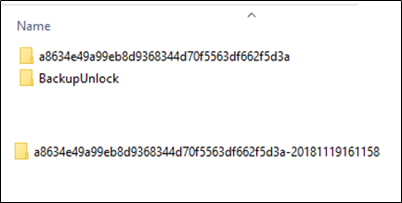
8. From here, you can load the unlocked backup into iBackupBot or your tool(s) of choice (iExplorer, etc.). Note: Some commercial tools HATE this format and will not support it. The free ones seem happy enough!
Now let’s get to that file you care about. Once your backup or image is loaded into your tool, you need to locate the following file: /Library/Preferences/com.apple.purplebuddy.plist. I normally just search for purplebuddy.
This plist stores the SetupState of the device which will tell you how the device was setup by the user.
If the user selected to restore a backup from iCloud, the com.apple.purplebuddy.plist will show:
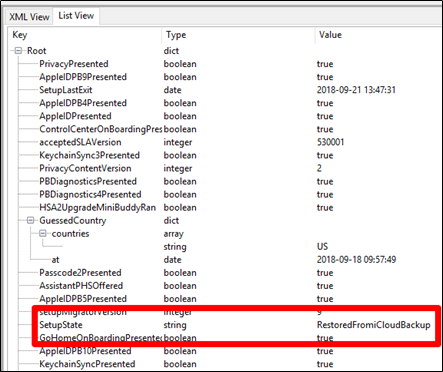
If the user setup the iPhone using iTunes, the com.apple.purplebuddy.plist will show:
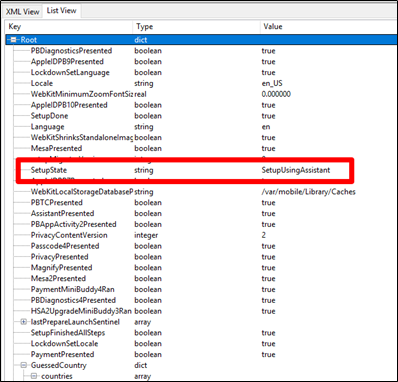
It is worth noting that I am testing on an iOS 12.1.x device and I restored from iTunes in 2 ways to obtain these results. First, I wiped and set up via iTunes and then I also forced a restore of a backup via iTunes. I wanted to be sure the SetupState didn’t change. If you find that the user restored from iCloud, consider pulling cloud data if you are legally capable of extracting that form of evidence. Should you find the user restored from iTunes, you now have to find that host computer to do analysis on other potential backups. This is where the fun begins!
Bottom line, Apple has a ton of plists that are relevant. You need to hunt for them. Do a keyword search, dump your device (yep, use the free way I described above) and VALIDATE!!!
If you want to watch the webcast, check it out here: https://www.youtube.com/watch?v=AC2TpWsLPLQ
CAUTION: iBACKUPBOT and iOS10+ potential issues.
Below I am attempted to do the same thing with iBackupBot, but I ran into iOS version issues.
- Launch iBackupBot
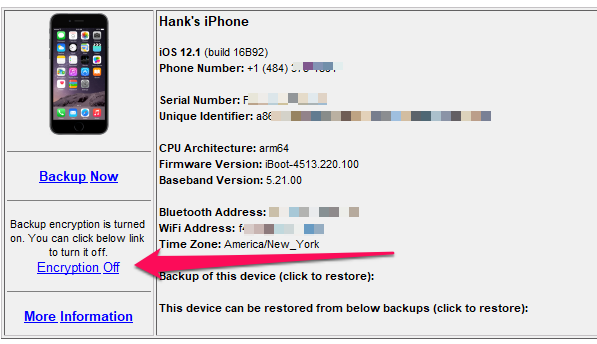
- Make sure you Trust the computer on the iPhone.
- Create an encrypted backup. Notice that the tool is telling you that Backup encryption is turned on? This is good.
4. Select where to save the backup image. I recommend into your case directory for the investigation.
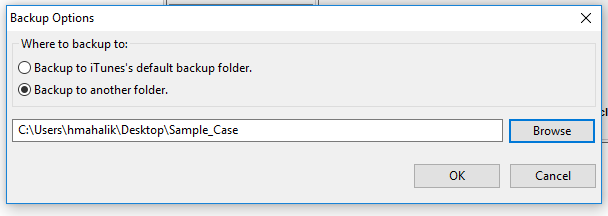
5. The backup will be created and then you can open it in iBackupBot for analysis. Once the backup is complete, it will prompt you to open it. If you have issues, this is an iOS10 error from what I have seen. :/ At this point, revert to iTunes.
Thanks for your research!
Is there a way to determine the exact time for when the phone have used the setup from iTunes or icloud?
Sounds like an excellent follow up blog!
Thank you Heather as always!!
I am going to run some testing on this issue on a couple of cases for some older iOS versions…Has there been any updated blog on this topic that I am missing? Thanks, Chris
11/10
Thank you Heather.
Nicely illustrated guide Heather. Keep writing.
Does anybody know if the dates are in UTC or local time? I don’t have my test phones with me.
Thanks!
Ed