I immediately installed and started using iOS 10.0.1 when the full release was available. For this testing, I used my non-jailbroken iPhone 6S and iTunes 12.4.2.4 with the addition of free and commerical tools. My intention is to share my initial thoughts on what is different in iOS 10 and what to expect when you see a device running this version. For more in depth details, analysis tips and tricks on iOS, refer to for585.com/course.
I expected major artifact location changes in iOS 10. I based this assumption on the fact that iOS 7 to iOS 8 was drastic in artifact changes. Nothing really changed when we upgraded to iOS 9, so I assumed… I’m happy to report that upon my initial research, I haven’t found drastic changes for most files of interest. I plan to keep digging here, just to be sure. As capabilities increase, we know that log files and usage artifacts are left on the device. These need to be researched further.
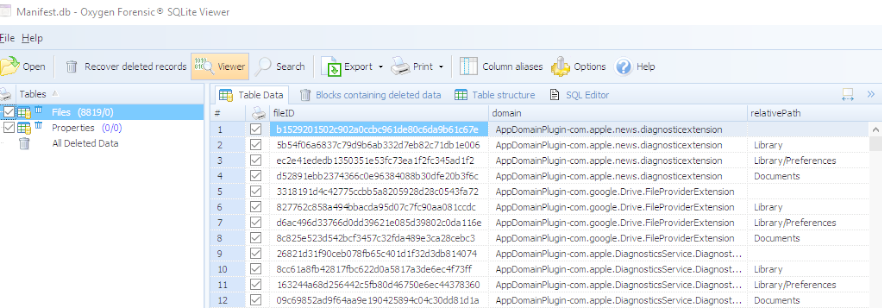
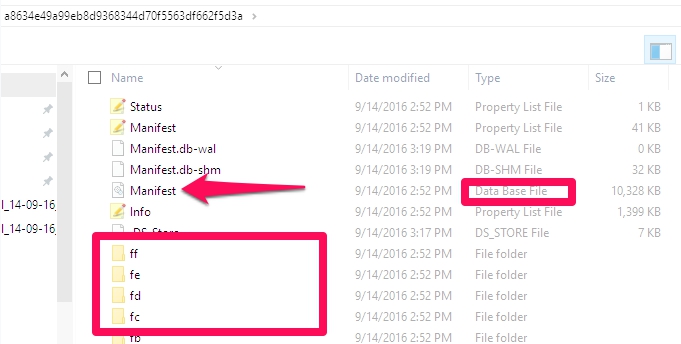
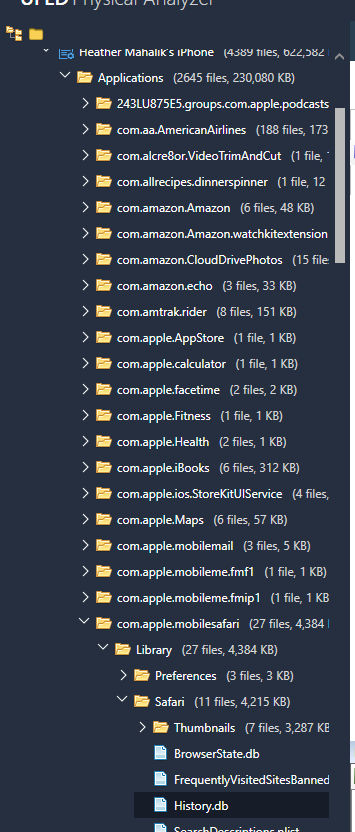
One major change I have noticed is with the structure of the iOS device backup. Below is an example of the new file structure.
A few things of interest:
- The Manifest.mbdb is now a SQLite database file – Manifest.db
- Instead of seeing all of files or “strings of letters” representing backup file contents, you now have folders containing these files, as shown above in the boxed area.
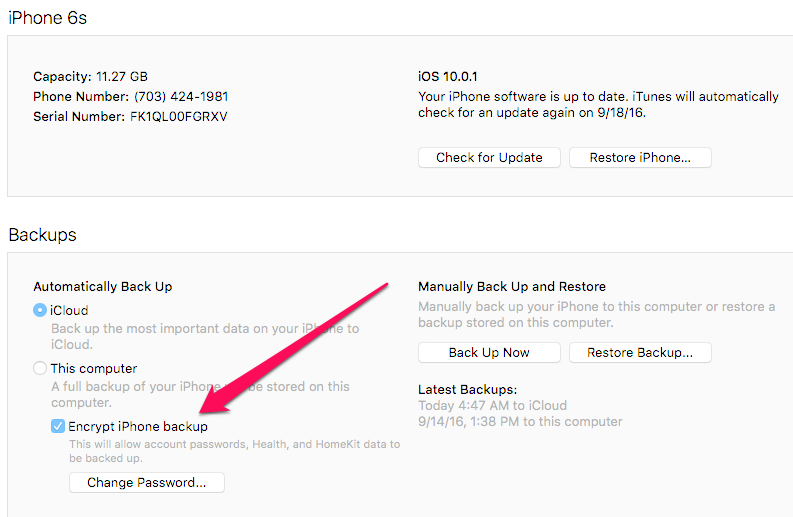
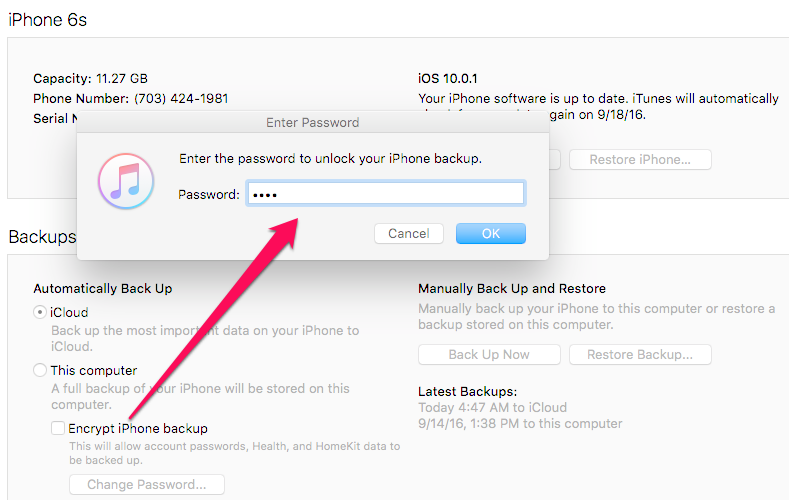
Once I had my backup, I starting digging through the files and panicked! Everything of interest appeared to be encrypted. This includes simple things like contacts, call logs, SMS and locations pulled from Apple maps. I frantically sent a Tweet seeing if this is what others were seeing and heard nothing. My tools all flopped. After the panic subsided, I decided to launch iTunes and take a look at my settings. Here is what I saw… The pesky box to Encrypt iPhone backup was checked even though I have been backing up to iCloud for as long as I can remember. Good think I remembered the password.
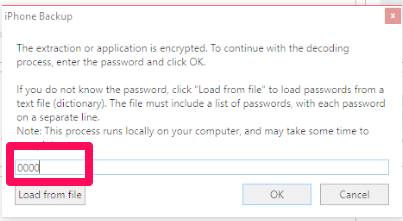
I was confused by this for several reasons. One, most of the commercial tools prompt you to enter a backup password and decode the data when this setting is enabled. Also, encrypting a backup and knowing the password provides us additional access to data – not blocks us from it! What could be going wrong? Could it be examiner error? Next, I did what most examiners would do and attempted to force my tools to parse this image. I launched UFED Physical Analyzer, IEF and BlackLight and entered the password (don’t worry, my passwords are much stronger than this, but I used a “dummy” one for this example.)
To my surprise, all of the databases of interest were still encrypted even after I asked the tool to decrypt my data with the correct passcode. To my dismay, nothing of interest was parsed, other than the Info.plist and Manifest.plist files. Even the Manifest.db was encrypted. Below you can see that the file system was parsed and accessible, but the databases and files of interest were encrypted, so this isn’t very helpful.
(Once opened, the History.db looked like this)
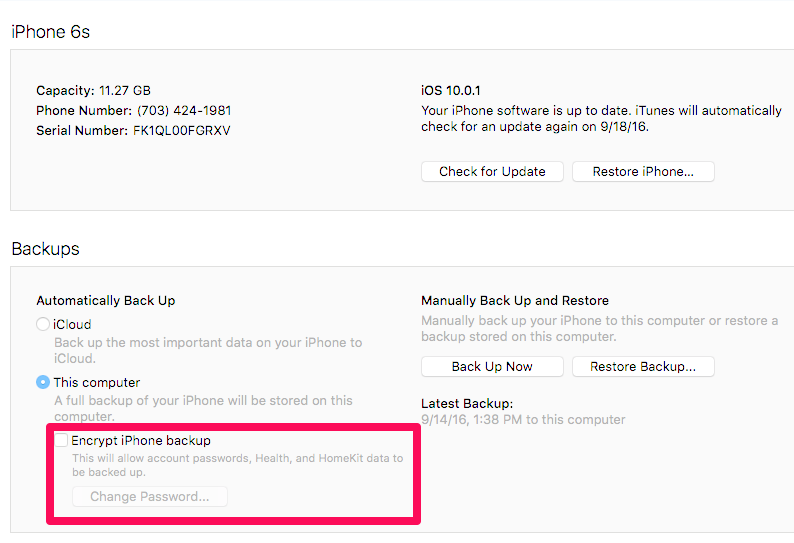
So now what? If you know the user’s backup password or can crack it, the password can be removed in iTunes. I tried this and then backed my phone up again.
First, I launched iTunes and unchecked the box for Encrypt iPhone Backup. I correctly entered my password.
The encryption was removed.
When I loaded this unencrypted version of my iOS backup file into forensic tools, some crashed, but I did have success in others. The first think I noticed was that the Manifest.db was no longer encrypted.
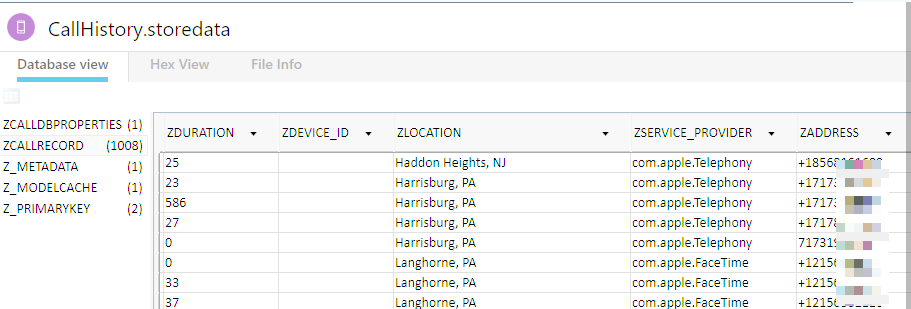
This gave me hope. I started examining the files that were previously encrypted within the iOS backup and found that they too, were accessible. Below, the CallHistory.storedata shows my call logs. When I initially created my backup, this file, like the Safari History.db, was encrypted!
I have reported these issues and concerns to the vendors and they are working on the issue. Here are some things they provided me in the meantime.
- Do not update to the latest version of iTunes if you are creating backups as forensic images. It causes issues.
- Do not select to “Encrypt” the backup in Physical Analyzer when obtaining an Advanced Logical Extraction. That too will render your data encrypted.
- Hope that the user never used iTunes encryption!
If you come across an encrypted iOS backup file, try to crack it. Personally, I rely on Elcomsoft tools to handle this. If you crack the password, you will manually have to remove the iTunes restriction and back the data up again until the tools adapt to handle iOS 10 backup file encryption.
In the meantime, practice on your own device and sign up for FOR585 Advanced Smartphone Forensics, where we cover topics like bypassing encryption and cover the cool artifacts of iOS. Happy iOS hunting!


Hi, I am trying to restore a backup file on my iPhone but it keeps asking me for a password. I didn’t set any password when backing the data. Is there a way to find out what could be my password from any files from the backup?
Any help would be appreciated, Thanks!
Try to crack a backup with Elcomsoft if you can. They will give you a demo.