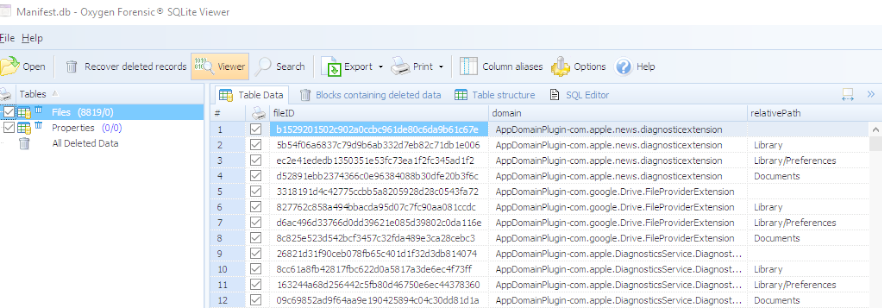
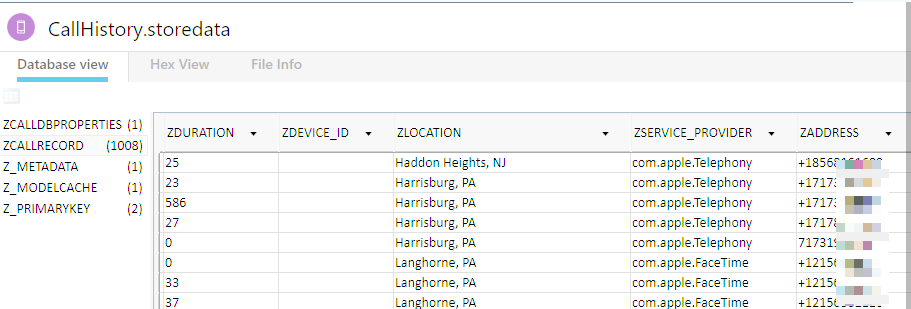
Happy Friday everyone. After my post last week, I was in touch with several vendors about what was occurring, my thoughts and how they intended to fix the problem when it comes to accessing the backup file data. Since then, two vendors (Cellebrite and Elcomsoft) reached out with an updated solution. I tested these tools over the last two days and want to share my results. I used Cellebrite Physical Analyzer v 5.3.5.10 (soon to be released), Elcomsoft v6.10 and iTunes 12.5.1 as well as the previous iTunes version to be thorough.
What changed since the last blog?
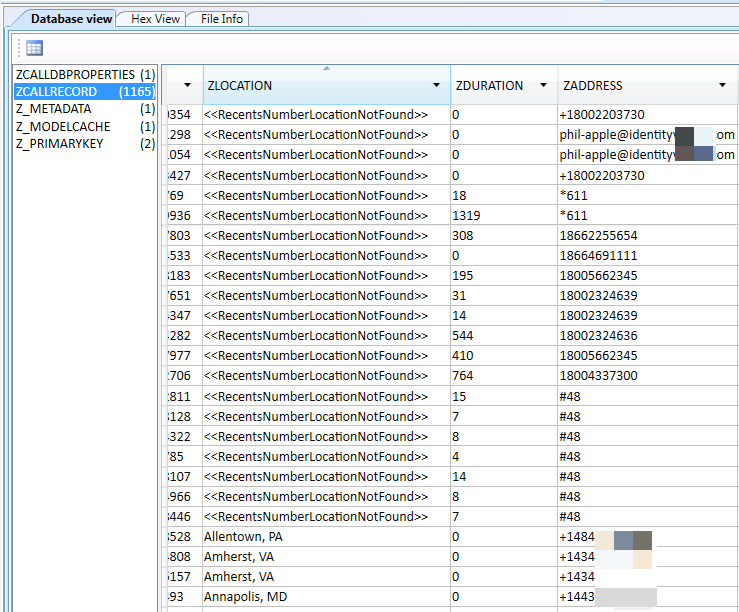
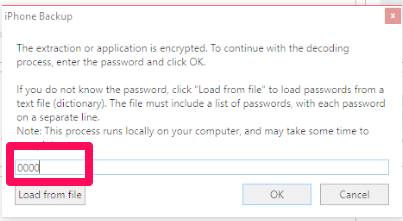
First, if an iOS10 backup file was encrypted with iTunes, you do not need to assume you cannot get into that data. (This was the case in my previous blog. Even if the password was known, the tools were choking on the data). If you can crack the password, Cellebrite’s UFED Physical Analyzer will properly decrypt this data. I bet you are now wondering how I cracked the encrypted iOS 10 backup files? I used Elcomsoft Phone Breaker v 6.10.
Cracking an encrypted iOS10 backup file
I set three different passwords to test. The first was 0000 and Elcomsoft laughed at this and provided the password before I could even sit back in my chair to watch. I then updated iTunes and changed my password to “hank” – this password didn’t even take a full second to crack.
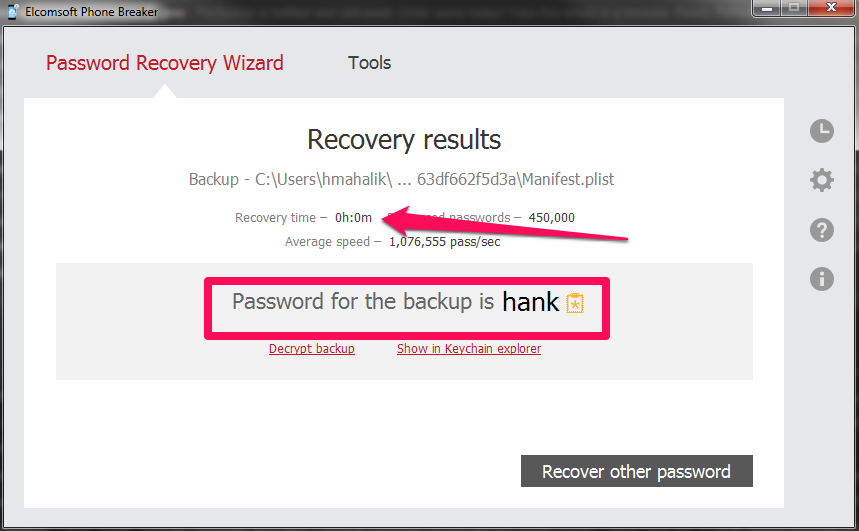
Maybe their claims are true that they will crack a passcode the fastest due to a vulnerability they found in the hashing of the passcode.
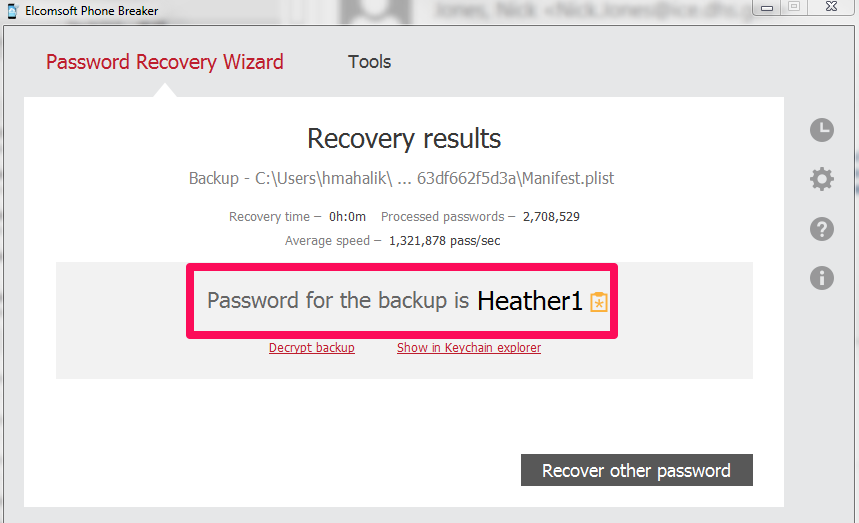
I then set a more difficult password “Heather1” and backed up my data using iTunes. Elcomsoft is saying that there is 87 years remaining for a brute force attack, so I am not going to wait. What should you do here? Try a dictionary attack! It’s much more effective with passwords such as “Heather1” when compared to Brute Force. When I changed to dictionary attack, this password was crack in less than 1 second! As a side note, I relied on the English dictionary and did not create anything custom for this test.
So, we have the password, what about the encrypted databases?
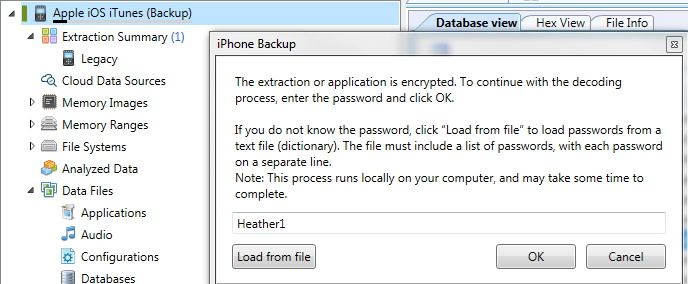
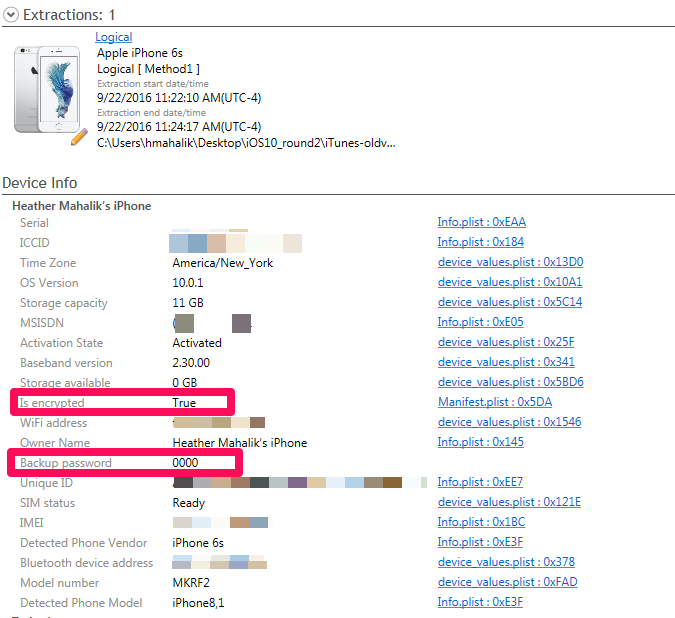
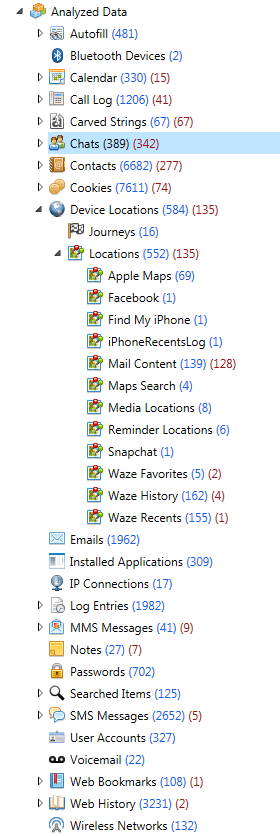
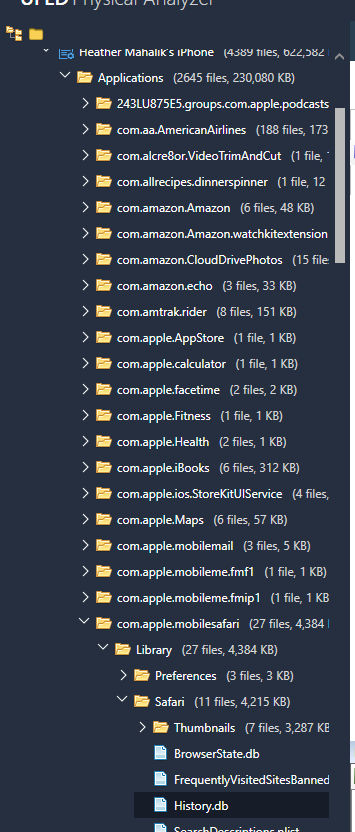
I was able to successfully parse all of the iOS10 backup files that I created over the last two days, containing various backup passwords, as well as the ones that were created for my previous blog post. As long as Physical Analyzer had the password, the data was decrypted and parsed. Make sure you are using Physical Analyzer v5.3.5.10 or later (assuming you have tested and validated the latest versions).
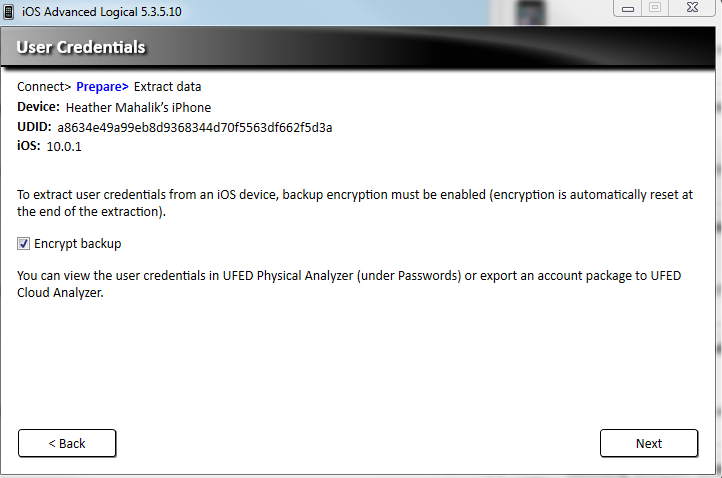
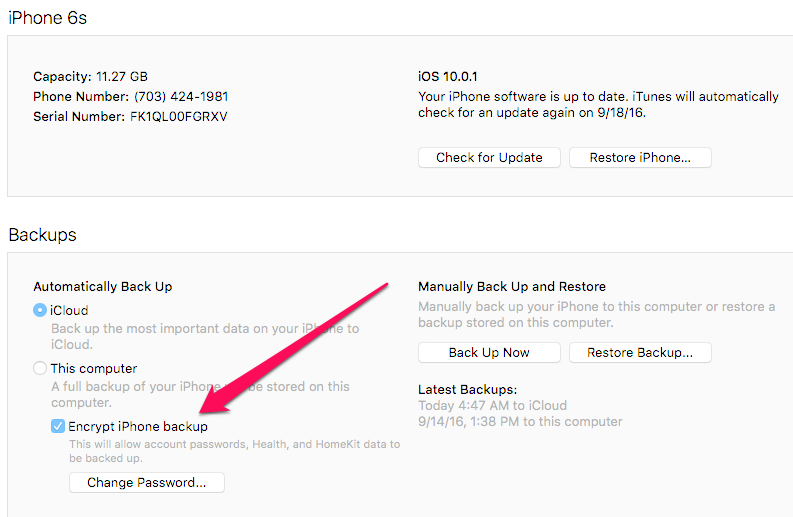
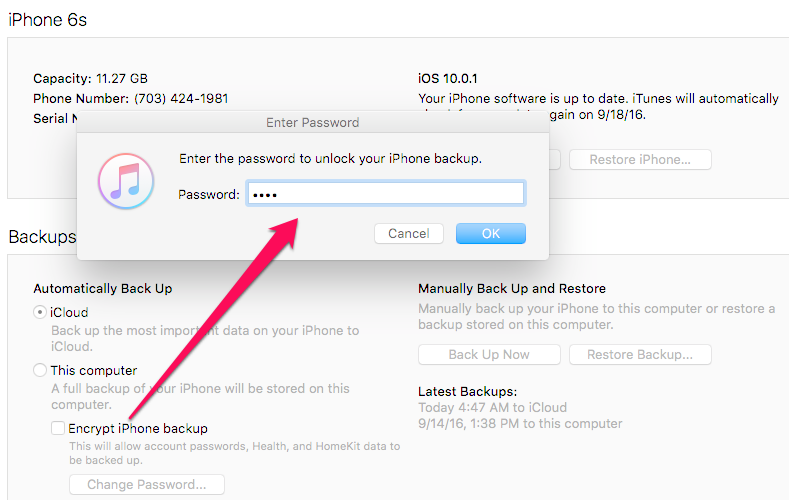
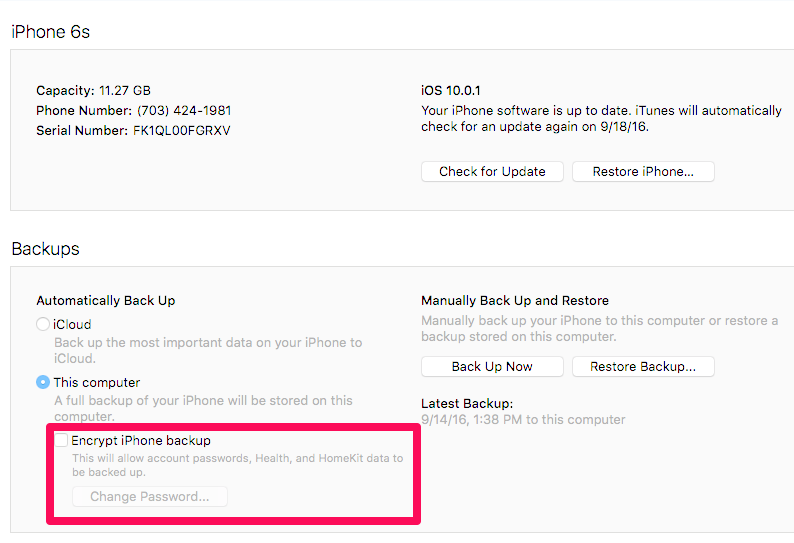
When attempting an Advanced Logical in Physical Analyzer, the option to encrypt the backup is provided if the backup has not been encrypted via iTunes by the user. You should select this option. If not, you will not get the data protected by the keychain. I selected to Encrypt my backup as shown below.
As stated in my last post, this was not an option with iOS10. Cellebrite has fixed this issue and all of the data will be parsed and decrypted. Additionally, if you are prompted for the users iTunes backup file password (the one you cracked with Elcomsoft), Physical Analyzer will parse the data when the password is correctly entered whether you selected an Advanced Logical Extraction or to add an iTunes backup file into the tool for analysis.
To be thorough, I tested the following in physical analyzer: